AirDrive Forensic Keylogger Module
The AirDrive Forensic Keylogger Module is an ultra-small USB keylogger module, only 0.5" (12 mm) in length and width. It can be accessed with any Wi-Fi device such as a computer, laptop, tablet, or smartphone.
Records keystrokes from any USB keyboard
Quick and easy installation inside a keyboard
Smallest keylogger module on the market, only 0.5" (12 mm) long
Stores 8000 pages of text
16MB internal flash memory
100% stealthy, undetectable for security software
Supports over 40 national keyboard layouts
Compatible with barcode readers
Works as a Wi-Fi hotspot
Connect from any computer, smartphone, or tablet
Access keystroke data from web browser, no software or app necessary
Retrieve data remotely without touching the device
Simple and clear WWW interface
Supports WEP, WPA, and WPA-2 network security
Memory protected by hardware encryption
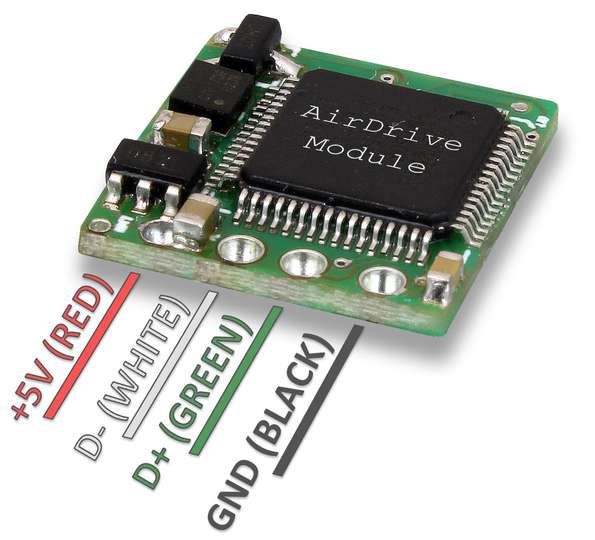
Quick installation
The AirDrive Forensic Keylogger Module is very easy to install inside any USB keyboard. Open the keyboard, tap onto power and the D+ and D- signals, and you're ready to go. No need to cut the wires, just ensure electrical contact exists.
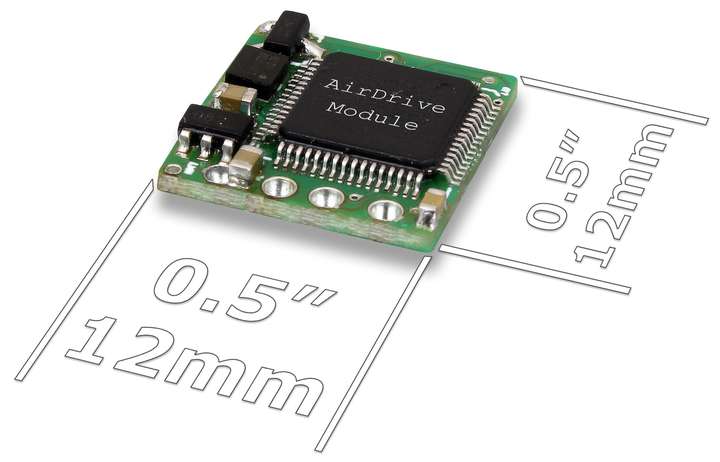
Size
The AirDrive Forensic Keylogger Module is 0.5" (12 mm) in length and width, making it easy to mount in literally any USB keyboard.

Easy access
All AirDrive devices act as Wi-Fi hotspots. You can connect to them with any Wi-Fi device, such as a smartphone, tablet, or laptop without even touching the device! The AirDrive device will then present a webpage with the data log and configuration options. No additional software or drivers necessary.

Retrieve data remotely
Unlike traditional keyloggers which work as USB flash drives, you don't need to have physical access to an AirDrive Keylogger to retrieve the logged data. Simply connect to it over Wi-Fi, download the log file, and you're done. You can then hide the keylogger by erasing the log, disabling further logging, or even hiding the WLAN network.
Compatibility
The AirDrive Keylogger family is compatible with all types of USB keyboards and barcode readers. Just connect the keylogger in-line with the keyboard, and all keystroke data will be recorded. The keylogger is 100% stealthy and does not pop-up as a system device.

Highly configurable
The AirDrive Keylogger is a powerful surveillance and security tool. The web interface allows to configure the Access Point WLAN settings, as well as a keystroke logging options. Over 40 national keyboard layouts are supported, including the most popular languages and keyboard layouts used throughout the world.

The Pro version advantage
The Pro version adds a powerful set of features centered around the capability to act both as a Wi-Fi hotspot, and a Wi-Fi device with Internet connectivity. This unleashes a broad set of options, such as email reporting, time-stamping, and live data streaming.
Important Legal Notice
The usage of a keylogger is fully legal as long as a clear notice is displayed, informing the user of the monitored equipment about the presence of a keystroke logger. We encourage the use of this equipment only for the purpose of monitoring your own computer, especially for protecting children against online hazards. It is NOT LEGAL to use a keylogger for the purpose of intercepting third party data, especially passwords, banking data, confidential correspondence, etc. If in doubt, please seek legal advice before using a keystroke logger. A good starting point is the U.S. Department of Justice Letter on Keystroke Monitoring and Login Banners, according to which a clear notice should be displayed, warning that user keystrokes may be logged.

Keyboard compatibility limitations
The device will work with almost all types of physical USB keyboards (it won't work with internal laptop keyboards). It works fine with wireless keyboards, with exception of Bluetooth keyboards. It won't work a few types of keyboards with built-in high-speed USB hubs (primarily Apple A1243 and Dell KB522), for which the Mac/MCP series should be used. Support for some gaming keyboards is not fully guaranteed, as they often use proprietary protocols.















